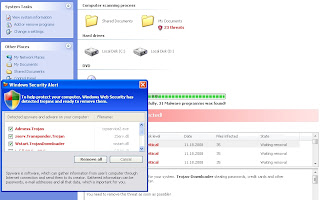
They are back, with a currently ongoing money mule recruitment campaign, this time not just attempting to recruit gullible users, but also, serving client-side exploits (CVE-2009-1492; CVE-2007-5659) through an embedded javascript on each and every page within the recruitment site.
Let's dissect the campaign, expose the client-side exploits serving domains, the Zeus-crimeware serving domains parked within the same netblock as the mule recruitment site itself, to ultimately expose a bogus company for furniture hosting a pretty descriptive cv.exe that is dropped on the infected host.
Initial recruitment email sent from financialcefin@aol.com:
Hello, Our Company is ready to offer full and part time job in your region. It is possible to apply for a well-paid part time job from your state. More information regarding working and cooperation opportunities will be sent upon request. Please send all further correspondence ONLY to Company's email address: james.mynes.cf@gmail.com Best regards
Response received:
Greetings,
Cefin Consulting & Finanace company thanks you for being interested in our offer. All additional information about our company you may read at our official site. www.ceffincfin.com Below the details of vacancy operational scheme:
1. The payment notice and the details of the beneficiary for further payment transfer will be e-mailed to your box. All necessary instructions regarding the payment will be enclosed.
2. As a next step, you'll have to withdraw cash from our account.
3. Afterwards you shall find the nearest Western Union office and make a transfer. Important: Only your first and last names shall be mentioned in the Western Union Form! No middle name (patronymic) is written! Please check carefully the spelling of the name, as it has to correspond to the spelling in the Notice.
4. Go back home soonest possible and advise our operator on the payment details (Sender’s Name, City, Country, MTCN (Money Transfer Control Number), Transfer Amount).
5. Our operator will receive the money and send it to the customer.
6. Please be ready to accept and to make similar transfers 2-5 times a week or even more often. Therefore you have to be on alert to make a Western Union payment any time.
 Should you face any problems incurred in the working process, don’t hesitate to contact our operator immediately. If you have any questions, please do not hesitate to contact us by e-mail. If you have understood the meaning of work and ready to begin working with us, please send us your INFO in the following format:
Should you face any problems incurred in the working process, don’t hesitate to contact our operator immediately. If you have any questions, please do not hesitate to contact us by e-mail. If you have understood the meaning of work and ready to begin working with us, please send us your INFO in the following format:1) First name 2) Last name 3) Country 4) City 5) Zip code 6) Home Phone number, Work Phone number, Mobile Phone number 7) Bank account info: a) Bank name b) Account name c) Account number d) Sort code 8) Scan you passport or driver license
2010 © Cefin Consulting & Finance
All right reserved.
Money mule recruitment URL: ceffincfin.com - 93.186.127.252 - Email: winter343@hotmail.com - currently flagged as malicious.
Once obfuscated, the javascript attempts to load the client-side exploits serving URL click-clicker.com /click/in.cgi?3 - 195.78.109.3; 195.78.108.221 - Email: aniwaylin@yahoo.com, or click-clicker.com - 195.78.109.3 - Email: aniwaylin@yahoo.com.
Sample campaign structure:
- click-clicke.com /cgi-bin/plt/n006106203302r0009R81fc905cX409b2ddfY0a607663Z0100f055
Parked on the same IP (91.213.174.52) are also the following client-side exploit serving domains:
click-reklama.com - Email: tahli@yahoo.com
googleinru.in - Email: mirikas@gmail.com
Within AS29106, VolgaHost-as PE Bondarenko Dmitriy Vladimirovich, we also have the following client-side exploits/crimeware friendly domains:
benlsdenc.com - Email: blablaman25@gmail.com
nermdusa.com - Email: polakurt69@gmail.com
mennlyndy.com - Email: albertxxl@gmail.com
kemilsy.com - Email: VsadlusGruziuk@gmail.com
benuoska.com - Email: godlikesme44@gmail.com
Name server of notice ns1.ginserdy.com - 93.186.127.205 - Email: albertxxl@gmail.com and ns1.ndnsgw.net - 195.78.109.3 - Email: aniwaylin@yahoo.com. have been also registered using the same emails as the original client-side exploit serving domains.
Sample detection rates, and phone back locations:
- cefin.js - Troj/IFrame-DY - Result: 1/42 (2.39%)
- clicker.pdf - Exploit.PDF-JS.Gen; Exploit:Win32/Pdfjsc.EM - Result: 21/42 (50.00%)
- clicker2.exe - TR/Sasfis.akdv.1; Trojan.Sasfis.akdv.1; Trojan.Win32.Sasfis.akdv - Result: 18/42 (42.86%)
- cv.exe - Trojan.Siggen1.15304 - Result: 3/42 (7.15%)
- 1.exe - Suspicious:W32/Malware!Gemini - Result: 4/42 (9.53%)
Upon execution, the sample phones back to Oficla/Sasfis C&C at socksbot.com /isb/gate.php?magic=121412150001&ox=2-5-1-2600&tm=3&id=24905431&cache=4154905385& - 195.78.109.3 - Email: aniwaylin@yahoo.com which drops pozitiv.md/master/cv.exe - 217.26.147.24 - Email: v.pozitiv@mail.ru from the web site of a fake company for furniture (PoZITIVe SRL).
Interestingly, today the update location has been changed to tds-style.spb.ru /error/1.exe. Detection rate:
- 1.exe - Suspicious:W32/Malware!Gemini - Result: 4/42 (9.53%)
Keeping the money mules on a short leash series, are prone to expand. Stay tuned!
Related coverage of money laundering in the context of cybercrime:
Keeping Money Mule Recruiters on a Short Leash - Part Three
Money Mule Recruiters on Yahoo!'s Web Hosting
Dissecting an Ongoing Money Mule Recruitment Campaign
Keeping Money Mule Recruiters on a Short Leash - Part Two
Keeping Reshipping Mule Recruiters on a Short Leash
Keeping Money Mule Recruiters on a Short Leash
Standardizing the Money Mule Recruitment Process
Inside a Money Laundering Group's Spamming Operations
Money Mule Recruiters use ASProx's Fast Fluxing Services
Money Mules Syndicate Actively Recruiting Since 2002
This post has been reproduced from Dancho Danchev's blog. Follow him on Twitter.